Cybersecurity Conundrum
McCombs experts weigh in on the growing digital threat.
By Mary Ann Roser
THE NEWS THAT Russians hacked the Democratic National Committee during last year’s presidential campaign hit like an earthquake that won’t stop rumbling. The aftershocks include more startling news of massive cyber breaches.
In March, WikiLeaks released thousands of documents purported to be CIA hacking tools, followed by another release that suggested the CIA’s own hacks could be disguised as actions by Russia or another country. Also in March, two Russian intelligence agents and two criminal hackers were arrested in the 2014 Yahoo breach of 500 million accounts.
By now, the American public seems to have been shaken awake to the significance of data protection issues along with companies that were complacent or loath to invest in cybersecurity.
Experts say they hope the attention will lead to more online vigilance. They predict that cyberattacks will happen more often across government, corporate, and personal digital space, while those who guard the data acknowledge they are playing defense in an increasingly high-stakes game.
Tom Molden, MBA ’98, an information security executive at General Motors, along with other McCombs experts in the cybersecurity field, says that threats are ever present. “We’re definitely in an ever-evolving threat landscape, with threat actors who get more sophisticated every day,” Molden confirms.
At the GM IT Innovation Center in North Austin, experts manage a variety of security controls, monitoring network traffic, scanning for and remediating vulnerabilities in the systems infrastructure, and analyzing anomalous online activity. It’s all part of a day’s job. And it’s never done.
Data Security Landscape
While the federal government does have some policies that some industries are required to meet regarding data security, in most cases, states are left to set cyber rules and police businesses. And although experts say they don’t see strong enforcement of such policies, many of them also don’t want to see a federal law prescribing cybersecurity requirements.
The field is changing rapidly, and there is no “one-size-fits-all solution,” cybersecurity experts say. Cyber criminals, meanwhile, can spend a small amount on a hacking kit and reap big returns selling the data on the underground market.
As technology becomes more pervasive in the world, the volume of targets and motivations for attacks is rising. Public utilities, industrial environments and transportation services are increasingly at risk from hackers; and the threat goes beyond theft of personal data, to include theft of trade secrets and disruption of operations.
“In addition to confidentiality, companies need to protect the integrity and availability of their information.” — Tom Molden
Christina Buss Pucheu, BBA ’10, a cybersecurity and privacy manager at accounting and consulting giant PwC in Dallas, says she has noticed companies spending slightly more on security in recent months. Even so, no system is perfect.
Consequently, companies walk a tightrope between how much to invest in cybersecurity and the cost of a potential breach. It’s a delicate balancing act. The cost of cyberattacks has risen 200 percent over a five-year period, Hewlett Packard Enterprise said in a report last year, to $450 billion worldwide. That’s expected to reach $2.1 trillion by 2019.
“It’s going to get worse,” warns Andrew Whinston, McCombs professor of Information, Risk, and Operations Management, who researches cybersecurity issues.
“As long as people can make money from stealing data, they will do it. Ultimately, we’re going to have to come to terms with the idea that we don’t have an effective way to deal with cybersecurity.”
— Andrew Whinston, director of the Center for Research in Electronic Commerce
The equation is lopsided in the criminal’s favor, says Joel Bauman, MBA ’02, the former vice president of corporate and business development at cybersecurity firm Cylance.
Bauman, who lives in San Jose, California, insists that companies need to direct more resources to preventing cyberattacks.
Adding to the challenge is an acute shortage of cybersecurity workers. Worldwide, there were 1 million vacancies in 2016, according to an estimate by Cisco, the San Jose tech giant.
“It’s very competitive to get cybersecurity talent,” PwC’s Pucheu says. “Growing new talent is difficult, but companies need to make their own investment to bridge that gap. It’s definitely a promising field, and it’s not going away.”
Emerging and Ongoing Threats
A year-end report from FireEye Inc., a leading cybersecurity solutions firm, says: “One sobering thought is that the threat activity we expect to hear about in 2017 may be taking place right now, with adversaries already inside many of the systems and networks necessary to achieve their mission.”

On average, it takes more than 200 days for a company to discover its system has been infiltrated, says Curtis Dukes, former director of information assurance at the National Security Agency. Cyber attackers are hard to beat because, unlike organizations that face many daily tasks from selling widgets to keeping their employees happy, they are single-minded about obtaining and exploiting sensitive information.
“The public is very naive about security,” says Eric Rattanavong, BBA 03, director of information security analysis at Capital One in McLean, Virginia. “They don’t clamor for better security because they don’t know what to fear.” Like other experts, Rattanavong is not surprised by the recent high-profile hacks and expects to see more cyber espionage.
Suspected Russian hackers, according to news reports, took down part of Ukraine’s power grid during the past two Decembers.
Rattanavong says. “The first militaristic volley isn’t going to be a missile; it’s going to be hacking — whether it’s hacking utilities, transportation, or communications.”
Ransomware, a malicious software that can freeze a computer system or encrypt data until the victim pays up, is an increasing threat, Rattanavong and other experts say. Hospitals and health care companies saw an escalation of ransomware last year. When faced with paying the ransom or being unable to function, they paid.
Ransomware was behind a power plant breach in Lansing, Michigan, last year when a utility company employee inadvertently opened an attachment with a virus. The company paid $25,000 to regain control of the system and spent $2.4 million beefing up its defenses. Power plant hacks are challenging because plants rely on proprietary control systems, which are highly complex and designed by outside vendors, says David Zahn, MBA ’99, chief marketing officer and general manager of the cybersecurity unit at PAS in Houston. So, if there is an unauthorized change in such a system, it can easily go undiscovered.
“Eighty percent of all cyber assets in a plant are proprietary systems, and, unfortunately, most plants don’t even keep an inventory of those systems,” Zahn says. “You can’t secure what you can’t see.” PAS provides security software to energy, power, and bulk manufacturing industries in more than 70 countries. Zahn notes that power plants aren’t alone in using proprietary control systems. They are used in everything from the rides at Disneyland to airplanes.
Threats from Within
Everyday objects, from home appliances and thermostats to jet engines to oil fields, are embedded with computing devices that enable them to send and receive data and are part of the “internet of things.” Increasingly, these objects are going to be hacked, experts say.

“In the rush to get tech into those products, they didn’t think about security until afterward,” says Dukes, who is now executive vice president of the nonprofit CIS, formerly known as the Center for Internet Security.
Global spending on IoT security is expected to be $434 million this year, according to an analysis by Gartner, a leading global advising and research information firm. By 2020, Gartner predicts that 25 percent of all identified attacks will involve IoT, but only 10 percent of security spending will be earmarked for it. At the very least, companies should encrypt sensitive data and transmissions, including any kept on laptops, says Doug Landoll, MBA ’01, of Georgetown, Texas.

Through his company Lantego, Landoll develops and leads training for cybersecurity certification exams and helps companies detect cyber vulnerabilities. Obtaining an independent assessment is perhaps the single-most important step on a company’s path to greater security, experts say. Organizations can then prioritize how they’ll spend the money, says Landoll, who previously worked for the FBI and CIA.
“The standards, the controls, and the experts who know how to fix it are out there,” Landoll adds. “The problem is the organizations that recognize the threat and choose not to do something about it.”
Another weakness is that security staffs at medium-sized and smaller companies typically focus on outside threats, without understanding how insiders may do harm. At the time Edward Snowden accessed classified documents and made them public in 2013, the NSA hadn’t paid much attention to insider threats, either. Snowden was a systems administrator, a position that generally holds “the highest level of credentials” for access, Rattanavong says. “We are at that stage now where we have to monitor system administrators.”
He estimates that “probably less than a fourth” of all companies do that. As Zahn puts it, “You can build a moat around your castle and protect it from the bad guys getting in, but you also have to protect your castle from the guys inside who already have the keys to the kingdom.”

Educate Early and Often
Even employees who have no desire to cause harm can get careless with those keys and open an attachment, unwittingly enabling undesired access. Organizations need to constantly educate their employees — and consumers need to educate themselves — on how to avoid attacks, says Sean McCleskey, a lawyer and former Secret Service agent.
McCleskey is now director of organizational education and measurement at UT’s Center for Identity, which offers free educational information to consumers, businesses, and law enforcement.
McCleskey teaches a course on law and identity as part of a master’s program in identity management. He sees firsthand how freely people put out private information that could be compromised.
“I don’t think students and younger people have really appreciated how valuable their data is,” he says. “I don’t know if they realize, having grown up with social media, how much they’re freely giving away. How many identity answers have you revealed online?” He jealously guards his Social Security number and never puts it in his medical records, he says.
He advises computer users to check carefully before clicking to make sure a site’s address or unfamiliar email is legitimate. Landoll urges consumers to monitor their checking, bank, credit card, and online shopping accounts regularly and change their passwords frequently.
Protection through Regulation?
Whinston says he has done research on potential solutions and has evidence indicating the benefits of having the federal government set up an agency to monitor outbound spam from companies, a sign they’ve been breached.
Businesses would be required to report outbound spam, and the numbers would be publicly disclosed, giving consumers more information to help them decide where they may — or may not — want to shop. Furthermore, Whinston wants cyber insurance to be far more common. Businesses wanting the coverage would have to meet standards, and insurers would thrive or die based on how well they guard data.
In a similar vein, internet service providers would act like cyber insurance companies by protecting their customers from hacks. ISPs that don’t perform well would go out of business, Whinston says. Protecting data is one issue that attracts bipartisan support, but experts said they didn’t want to predict what the Trump administration will do about cybersecurity. In general, Trump has said that businesses should expect less business regulation, not more.
Just as rules to strengthen consumers’ privacy were to take effect in March, the Federal Communications Commission blocked them. Congress then voted to repeal the regulations, which would have required internet service providers, such as Verizon, to take “reasonable” steps to protect consumer data from being breached. The companies also can sell or use the data without seeking consent. Supporters said the rules would have stifled innovation and been more restrictive on ISPs than on companies like Facebook.
Technology Solutions
Companies, meanwhile, are not standing still. Many are looking to new technologies for solutions. As a report last year by PwC says, more and more businesses are turning to the cloud to secure their data:
“Many, in fact, are running data and workloads such as finance, operations, and customer service in the cloud. Even highly regulated businesses, including large financial services firms with very mature cybersecurity programs, are entrusting sensitive data to cloud providers.”
Those off-premises cloud storage services can also be combined with other innovative technologies. For example, several cybersecurity companies are buying artificial intelligence tools to detect abnormalities so they can catch criminals before they hack, rather than reacting to a breach, says Bauman, the former executive at Cylance, one of the first companies to develop AI software as “a core tool for security” in 2012.

The company’s technology can look at a billion files and “leverage machine learning to pull those files apart into component parts, like unraveling DNA into proteins,” Bauman says. “The company is trying to solve the problem of malware, to see if a file is malicious.”
The U.S. Office of Personnel Management used Cylance after the agency’s staggering 2015 hack that compromised data on individuals inside and outside the government. Cylance located the corrupted file that caused the intrusion, which had begun in 2014. In addition to AI, businesses and consumers might soon hear more about new efforts to authenticate identity and avoid fraud.
Lee Aber, BBA ’01, is vice president of security and risk management at one such digital identity verification company, ID.me. Aber says he worked at several Austin companies and Texas data centers where he learned the nitty-gritty workings of network security before consulting with federal agencies in Washington.
At ID.me in McLean, Virginia, members of the military and veterans can authenticate who they are online by going through a series of identity-proofing steps, just one time, to access benefits and other federal government services.
Aber says he thinks “companies need to find a way to securely ensure that it’s really you” so consumers can control their privacy when they interact online.
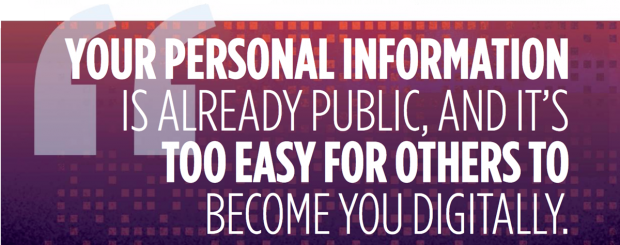
Other experts echoed that as ID.me prepares to launch in the private sector. “Your personal information is already public, and it’s too easy for others to become you digitally,” Aber says.
The security teams at GM are constantly evaluating new technologies, including AI, Molden says. At the same time, he says, businesses should be collaborating and “sharing intelligence with each other.”
From the spring 2017 issue of McCOMBS, the magazine for alumni and friends of the McCombs School of Business.
About this Post
Share:


